The Cost of a Single Broken API
In 2022, Optus – a major Australian telecom – suffered a breach that exposed the data of over 11 million customers.
The root cause? A single, unauthenticated API endpoint.
What looked like a simple oversight turned into a nationwide scandal, regulatory fallout, and shattered consumer trust.
Fast forward to 2025, and APIs have only grown more powerful – and more dangerous. According to Gartner, APIs remain the #1 application attack vector, and global API-related security incidents are now estimated to cost businesses up to $87 billion annually (Imperva/Thales).
Why? Because APIs aren’t just backend utilities anymore – they’re the front doors to your most sensitive data, your business logic, and your customer trust.
Yet many teams still rely on outdated security models that weren’t built for the way modern APIs are developed, deployed, and abused.
If you’re still protecting APIs with generic firewalls and static scanners, you’re not secure – you’re just lucky.
What Is API Security – and Why Should You Care?
APIs – short for Application Programming Interfaces – are the invisible engines behind nearly every digital interaction. From logging into a mobile app to booking a flight online, APIs quietly connect the front-end user experience to the backend systems that make it all work.
But with that power comes a serious risk.
API security is all about protecting these digital highways from misuse, manipulation, and attack. It includes the techniques, tools, and best practices designed to defend APIs at every stage – development, deployment, and runtime.
The rise of generative AI and autonomous agents has brought APIs into sharper focus. Every AI-powered feature – whether it’s analyzing data, generating content, or triggering automation – relies on APIs to function. A single insecure API can expose sensitive data or create dangerous loopholes for malicious actors and rogue bots.
As AI adoption accelerates, APIs are becoming the new attack surface. If your APIs aren’t secure, your entire digital infrastructure is at risk.
Why APIs Have Become the Prime Target
To understand why API security matters so much today, it helps to zoom out. Between 2016 and 2021, the number of API collections created by developers using Postman skyrocketed from less than half a million to nearly 46 million. That’s not just growth – it’s a revolution.
Three major shifts are driving this API explosion (as per Postman itself):
- Consumers are everywhere. We no longer use one device or one platform. From smart TVs to wearable tech, APIs power the multi-device experience.
- Architectures are changing. APIs are what allow modern microservices to talk to each other, replacing old-school monoliths.
- Infrastructure has moved to the cloud. APIs let teams launch new services without waiting for physical hardware, enabling speed and scale like never before.
But here’s the catch: Every API you publish is a potential entry point for an attacker.
What Makes APIs So Risky?
Unlike traditional web pages, APIs are designed to be accessed directly over the internet – often by other machines, apps, or services.. That means they:
- Expose sensitive data like user credentials, financial info, and PII.
- Control critical operations – from account changes to money transfers.
- Can be called repeatedly, often without rate limits or visibility.
Attackers know this, and they exploit it.
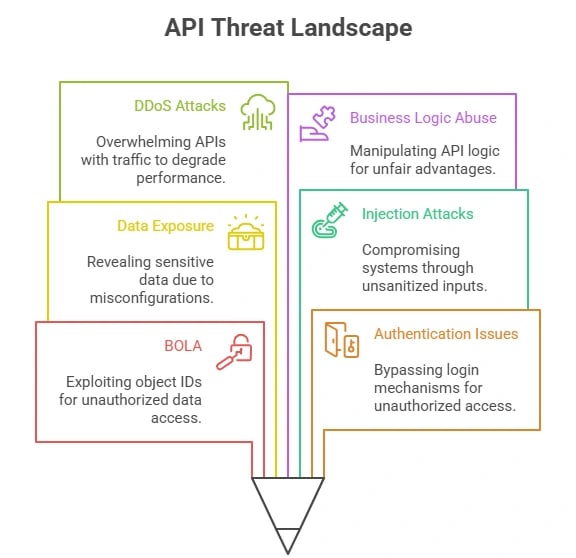
The Most Common API Threats
API attacks don’t always come with alarms or dramatic breaches. They’re often low-and-slow, highly targeted, and difficult to detect until it’s too late. Among these, one threat stands out as the most exploited in the real world:
- BOLA (Broken Object Level Authorization): The #1 API vulnerability. Attackers manipulate object IDs (like user IDs or transaction IDs) in API calls to access unauthorized data or functions. It’s deceptively simple, devastatingly effective, and hard to detect without deep business logic security.
Other widespread threats include:
- Broken authentication and authorization: Attackers bypass login mechanisms or privilege checks to gain access they shouldn’t have.
- Sensitive data exposure: APIs accidentally reveal personal, financial, or business-critical data due to misconfigurations or overly broad responses.
- Injection attacks: Inputs aren’t properly sanitized, allowing SQL, NoSQL, or command injections to compromise backend systems.
- DDoS and volumetric abuse: Attackers flood API endpoints with traffic to crash services or degrade performance.
- Business logic abuse: The most nuanced threat – exploiting how your API is supposed to work. Attackers manipulate pricing engines, exploit promo logic, or chain calls to gain unfair access.
Key Features to Look For in API Security Tools
Not every API security tool is built the same. While many offer overlapping capabilities on paper, only a handful deliver effective protection across the full lifecycle of an API. These are the core features to evaluate when selecting a modern API security platform in 2025.
- API Discovery
Automatically identifies every API in your environment, including unmanaged, undocumented (shadow), and deprecated (zombie) endpoints. This is essential for visibility and forms the foundation of any security strategy. Many tools still struggle to reliably detect APIs deployed across hybrid or multi-cloud setups. - Business Logic Security
Most critical API breaches today don’t exploit technical misconfigurations – they exploit how the API is intended to work. Business logic security refers to detecting abuse patterns like broken object-level authorization (BOLA), excessive data access, or misuse of sequencing. As you will see in the list, only a few tools actually offer this level of contextual detection. - Threat Detection and Anomaly Analysis
A modern API security tool should detect abnormal behavior across APIs, users, and sessions using machine learning, traffic profiling, and statistical analysis. The goal is to spot attacks that don’t trigger known rules, such as low-and-slow scraping, bot behavior, or data exfiltration over time. - Real-Time Protection
Runtime protection should be flexible and adaptable, whether through inline blocking, rate limiting, or out-of-band alerting. The best tools allow teams to apply protection without disrupting valid traffic and offer deployment options that support scale and availability needs. - Security Testing: Shift Left and Protect Right
Effective tools support both pre-production security testing and production monitoring. This means integrating into CI/CD to test APIs during development and continuing to validate them in live environments. As you will see in the platform breakdown, only some vendors provide both proactively and continuously. - CI/CD and DevSecOps Integration
To keep up with modern release cycles, API security tools must integrate seamlessly with developer pipelines. Look for support for GitHub Actions, GitLab CI, Azure DevOps, and other automation tools to enforce policies, run tests, and raise alerts directly in the development workflow. - Compliance and Reporting
Strong reporting capabilities help organizations meet regulatory obligations such as SOC 2, PCI DSS, HIPAA, or GDPR. Security platforms should provide detailed logs, real-time alerts, policy tracking, and audit-ready dashboards. - Runtime Monitoring and Drift Detection
Even after deployment, APIs continue to change. Effective solutions monitor for new endpoints, configuration drift, or traffic pattern anomalies. This ensures the security posture keeps pace with the application’s evolution.
And What Exactly Is Shift-Left Security?
Shift-left security means bringing security earlier (“left”) in the software development lifecycle. Instead of checking for vulnerabilities at the end, teams embed security into coding, API design, and CI/CD stages, when issues are easier and cheaper to fix. It’s a cornerstone of modern DevSecOps.
The Top 15 API Security Tools in 2025
With dozens of vendors entering the API security space, choosing the right tool isn’t just about popularity – it’s about understanding real-world use cases, technical maturity, and where each solution fits in your security architecture.
To bring clarity, we’ve mapped the API security landscape using five key domains that reflect how these tools operate:
- Full Lifecycle API Protection: Covers discovery, shift-left testing, runtime protection, and remediation.
- Runtime Threat Detection & Defense: Specializes in monitoring live traffic, detecting anomalies, and blocking malicious behavior in real time.
- Shift-Left Security & Developer Enablement: Helps developers catch issues early via CI/CD integration, spec validation, and pre-production testing.
- Business Logic & Advanced API Protection: Protects against contextual attacks like BOLA, abuse of workflows, and access manipulation.
- Open Source Tools: DIY, customizable tools for testing and inspection – ideal for red teams or budget-conscious teams.
Many tools span more than one domain. That’s why instead of forcing them into rigid tiers, we’ve ranked them based on how many of these domains they cover – giving you a clearer picture of their versatility.
Under each tool, we’ve also noted key differentiators that highlight what makes it stand out – whether it’s business logic mapping, LLM protection, or Go-based open-source flexibility.
This isn’t a one-size-fits-all ranking. The right choice for your team will depend on your architecture, security maturity, and development workflows – but this list is designed to make your decision a lot easier.
AppSentinels
Domains: Full Lifecycle API Protection, Runtime Threat Detection & Defense, Shift-Left Security & Developer Enablement, Business Logic & Advanced API Protection
Differentiators: AI-powered business logic graph, automated pen-testing, WAAP platform combining NG-WAF, agentless+agent options, Multi-Layer Defense (WAF, Bot, DDoS, Logic), 50+ integrations for instant onboarding
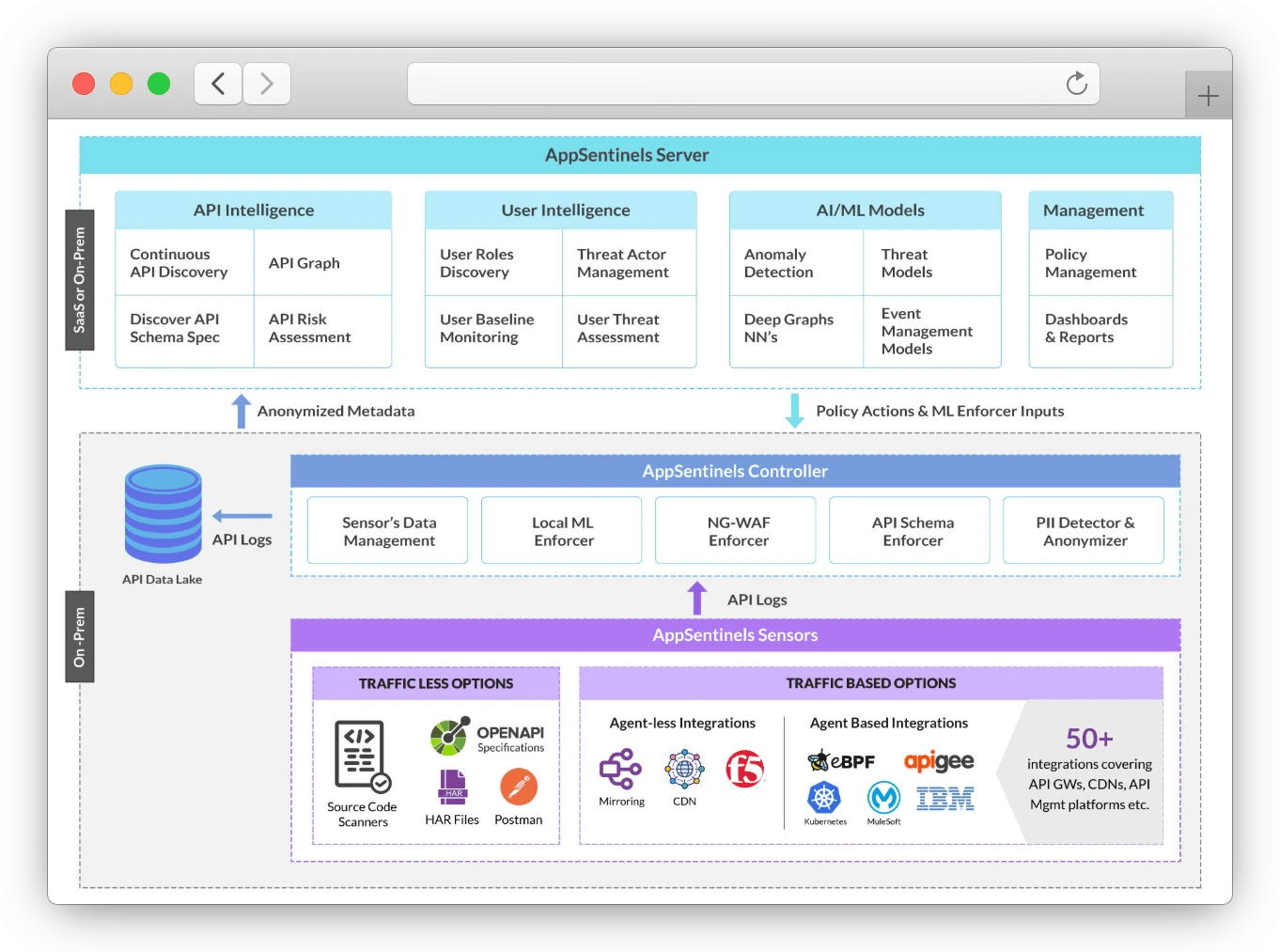
AppSentinels is a unified WAAP (Web Application and API Protection) platform and full-stack API security solution purpose-built for modern, API-first architectures. Unlike generic tools, it offers deep visibility into how APIs behave across applications – making it one of the few platforms that truly delivers context-aware business logic protection. With its scalable three-tier architecture, AppSentinels secures APIs from development to production through intelligent automation, AI/ML analytics, and seamless integration across hybrid environments.
Key Features:
- Business Logic Security: Understands application context across multiple APIs to detect BOLA, IDOR, and abuse of intended functionality.
- Fully Automated API Pen Testing: Simulates 24×7 ethical hackers with AI-driven fuzzing and logic flaw testing – even in production.
- WAAP Platform (NG-WAF + API Security + Bot Protection): Provides unified, multi-layer defense that blocks injection attacks, DDoS, botnets, and business logic abuse with minimal false positives.
- Shift-Left + Protect-Right: Integrates API scanning in CI/CD and continuously protects production traffic – closing the loop between dev and runtime security.
- 3-Tier Architecture: Built on a distributed 3-tier model (Sensors, Controllers, Servers) that scales to billions of API calls while maintaining policy-driven control and observability.
- Plug-and-Play Across 50+ Integrations: Supports frictionless deployment in hybrid, cloud-native, or on-prem environments with built-in connectors for popular API gateways, CI/CD pipelines, observability, and security tools.
- Protocol Coverage: Supports REST, SOAP, gRPC, and GraphQL APIs with deep inspection, adaptive risk scoring, and traffic normalization.
- Best Real-time runtime API security with traffic analysis, threat blocking, and data leak prevention, trusted by top app protection companies.
Figures:
- Protects over 100 billion API calls and 100,000+ endpoints every month.
- Named in the 2025 Gartner® Hype Cycle for APIs in two categories: API Threat Protection, as well as in API Security Testing
Pricing: Custom quote based on infrastructure, API volume, and feature requirements. Free trial and demo available upon request.
Visit AppSentinels for more information.
Traceable AI
Domains: Full Lifecycle API Protection, Runtime Threat Detection & Defense, Business Logic & Advanced API Protection
Differentiators: Deep observability, LLM/prompt injection protection, OmniTrace engine
Traceable combines observability and security to deliver a next-gen solution for API protection – ideal for microservices-heavy, cloud-native environments. It’s the first to offer dedicated LLM/prompt injection monitoring.
Key Features:
- OmniTrace engine: Full-stack tracing and ML-driven behavior detection.
- GenAI/LLM protection: Monitors prompt injection and hallucination risks.
- Broad compatibility: REST, SOAP, gRPC, GraphQL.
- Deep business logic defense: Maps and protects complex workflows.
- Spec compliance: Automatically generates OpenAPI specs and validates them.
Figures:
- Scales to support thousands of APIs across large and small organizations.
Pricing: Not publicly listed; contact sales for customized tiers.
Visit Traceable AI for more information.
Salt Security
Domains: Full Lifecycle API Protection, Runtime Threat Detection & Defense, Business Logic & Advanced API Protection
Differentiators: Massive API data lake, attacker timeline, CrowdStrike integration
Salt Security is a pioneer in AI-driven API protection, offering deep visibility and defense throughout the API lifecycle. It leverages a massive data lake to baseline behavior and catch anomalies before damage is done.
Key Features:
- AI-based runtime threat detection and attacker timeline visualization.
- API call sequence analysis to uncover business logic abuse.
- Full lifecycle support: Discovery, posture management, runtime prevention, and shift-left testing.
- Seamless integration: Native availability for CrowdStrike customers.
Figures:
- Founded in 2018, valued at $1.4B post-Series D.
- $271M+ funding raised.
Pricing: Custom model based on API traffic and enterprise needs. Free trial available.
Visit Salt Security for more information.
Wallarm
Domains: Full Lifecycle API Protection, Runtime Threat Detection & Defense, Business Logic & Advanced API Protection
Differentiators: API/WAF/bot combo, patented ML, SOC-as-a-Service
Wallarm provides a unified Web Application & API Protection (WAAP) platform – combining WAF, API security, and bot defense. It’s ideal for hybrid/multi-cloud environments.
Key Features:
- WAAP Platform: Combines NGWAF, API security, and bot mitigation.
- Comprehensive Discovery: Zero-deployment mapping for public APIs.
- Real-Time Protection: AI-based threat detection with OWASP Top 10 defense.
- Kubernetes & Cloud-Native Support: Easy DevOps integration.
- Automated IR: Policy updates and risk response without manual effort.
Figures:
- Trusted by hundreds of regulated industry teams.
Pricing:
- Free plan includes Host & API Discovery, WAF Testing, API Vulnerability Detection, and API Leaks Mitigation.
- Contact sales for an enterprise quote.
Visit Wallarm for more information.
Firetail
Domains: Full Lifecycle API Protection, Runtime Threat Detection & Defense, Business Logic & Advanced API Protection
Differentiators: Cloud-native observability, posture governance, runtime API security across hybrid and multi-cloud
Firetail is an API security platform specializing in observability, traffic analytics, business logic modeling, and compliance. It enables discovery, governance, and runtime protection across distributed and cloud-native environments.
Key Features:
- Continuous API Discovery: Maps and inventories APIs across AWS, Azure, GCP, Snowflake, and SaaS environments.
- Runtime Analytics: Monitors user behavior, service access, and sensitive flows to detect BOLA, injections, and credential threats.
- Posture Management: Identifies misconfigurations, excessive access, spec drift, and non-compliant endpoints.
- Automated Policy Enforcement: Applies access policies and rate limiting; integrates with CI/CD pipelines.
Figures:
- Secures billions of API calls per month
Pricing:
- Starter Plan: $22,000 per year ($2,000/month) for up to 50 APIs and 50 million API calls/month
- Business Plan: $44,000 per year ($4,000/month) for 100 APIs and 100 million API calls/month
- Enterprise: Custom pricing for advanced needs and integrations
Visit Firetail for more information.
Akamai API Security
Domains: Full Lifecycle API Protection, Runtime Threat Detection & Defense, Shift-Left Security & Developer Enablement
Differentiators: Global edge protection, attack pattern insights, Noname-powered lifecycle coverage
Enterprise-grade API security delivered at the edge. Built on Akamai’s global network, it offers anomaly detection, posture insights, and layered threat protection.
In June 2024, Akamai completed its $450 million acquisition of Noname Security. Noname’s technology now forms the backbone of Akamai’s API Security stack – combined with capabilities from its earlier Neosec acquisition. This unified platform spans the entire API lifecycle: from deep discovery (including shadow APIs) and posture management to shift-left testing in CI/CD pipelines, behavioral threat detection, and runtime protection.
Key Features:
- Auto-discovery of all API traffic.
- Behavioral threat detection + runtime abuse protection.
- Built-in compliance dashboards.
- Edge-native enforcement for global latency reduction
Figures:
- Processed 108B+ API attacks (Jan 2023–Jun 2024).
Pricing:
- Entry SaaS: ~$150,000/year (AWS Marketplace).
- Enterprise: Custom quotes.
Visit Akamai for more information.
Imperva API Security
Domains: Full Lifecycle API Protection, Runtime Threat Detection & Defense
Differentiators: Integrated WAF/API defense, compliance dashboards
Backed by cybersecurity veteran Imperva, this API solution integrates seamlessly with their leading WAF and DDoS offerings. It’s well-suited for enterprises needing centralized control across hybrid environments.
Key Features:
- Auto-discovery of all API traffic, including legacy and shadow endpoints.
- Runtime policies against OWASP Top 10 and zero-day exploits.
- Integrated WAF and DDoS protection.
- Real-time dashboards for risk visualization.
- Compliance-ready reporting (HIPAA, GDPR, PCI DSS).
Figures:
- The parent company was founded in 2002, with global deployment across finance, retail, and government sectors.
Pricing: Custom enterprise pricing. Demo available on request.
Visit Imperva for more information.
Cequence Security
Domains: Runtime Threat Detection & Defense, Business Logic & Advanced API Protection
Differentiators: Bot defense, behavioral AI, fraud protection
Cequence excels in behavioral API protection and is an industry leader in bot mitigation for public-facing APIs.
Key Features:
- Bot Defense: Blocks scraping, credential stuffing, and fraud.
- Unified Discovery: Surface maps and tracks internal/external APIs.
- Behavioral Fingerprinting: Persistent attack tracking across IPs.
- Flexible Response: Geo-fencing, deception, rate limiting.
- Deployment Options: SaaS, hybrid, and on-prem supported.
Figures:
- Adopted widely by financial services and large public apps.
Pricing:
- Pricing is not publicly available.
Visit Cequence Security for more information.
42Crunch
Domains: Shift-Left Security & Developer Enablement, Business Logic & Advanced API Protection
Differentiators: Contract audit, security score, quality gates in CI/CD
The definitive leader in shift-left API security, 42Crunch empowers developers with automated OpenAPI/Swagger specification auditing, vulnerability detection, and seamless CI/CD integration.
Key Features:
- API Security Audit: 300+ checks with actionable scoring and recommendations.
- Shift-left Testing: Real-time security feedback during design and code review.
- Security Gates: Prevents deployment of APIs with low security scores.
- CI/CD Native: Supports GitHub Actions, Azure DevOps, Jenkins, and IDE plugins.
- Micro-Firewall: Enforces schema-based runtime security.
Figures:
- Serves developers in large financial/enterprise organizations.
Pricing:
- Free Tier: Up to 100 audits/month.
- Single User: $15 / month
- Team Plans: $375 / month, for up to 25 devs and 10 APIs.
- Enterprise: Custom quotes.
Visit 42Crunch for more information.
APIsec
Domains: Shift-Left Security & Developer Enablement, Business Logic & Advanced API Protection
Differentiators: Automated security testing for APIs, CI/CD integration, business logic flaw detection
APIsec focuses on testing APIs before they go live. It runs automated security scans directly inside CI/CD pipelines – checking for OWASP Top 10 issues, broken authentication, and even logic-based vulnerabilities. The goal is to help teams catch issues early, without relying on manual pen-testing or adding too much overhead.
APIsec is focused on shift-left security. It doesn’t handle runtime traffic or live threat detection – instead, it’s best suited for teams looking to strengthen their APIs earlier in the development cycle through automated testing.
Key Features:
- Automated API security testing with every code push
- CI/CD-ready, works with common pipelines
- Covers both technical and business logic vulnerabilities
- Authenticated testing and support for complex workflows
- Reporting tools for compliance and tracking
- On-premises deployment available for regulated environments
Figures:
- Supports integrations with major CI/CD and ticketing systems.
Pricing:
- Free: Simple plan with basic features
- Pen Test Edition: $325/month per 100 endpoints
- Standard: $650/month per 100 endpoints
- Pro: $2,600/month per 100 endpoints
Visit APIsec for more information.
Escape
Domains: Shift-Left Security & Developer Enablement
Differentiators: Developer-first CI/CD API scanning, rich OpenAPI integration, code-to-cloud mapping
Developer-centric platform for shift-left API security. Escape focuses on automated, continuous security testing directly in the development pipeline, helping teams detect and remediate vulnerabilities before APIs are deployed.
Key Features:
- Automated API Security Scans: Detects OWASP API Top 10, business logic flaws, authentication issues, and data exposures with every code push.
- OpenAPI/Swagger Integration: Dynamically syncs specs and tests APIs using live or documented schemas.
- CI/CD Native: Compatible with GitHub Actions, GitLab CI, CircleCI, Bitbucket, Jenkins, and others.
- Code-to-Cloud Inventory: Maps source-defined APIs to live cloud endpoints to uncover shadow or zombie APIs.
- Developer Feedback: Surfaces results as code comments and tickets, integrated with dashboards and tooling.
Figures:
- Used by SaaS, fintech, and unicorn startups
Pricing:
- Escape offers 3 pricing tiers, including up to 15, up to 60, or up to 120 scanned applications.
- Contact sales for pricing offers.
Visit Escape for more information.
StackHawk
Domains: Shift-Left Security & Developer Enablement
Differentiators: Dev-centric DAST, CI pipeline ready
Modern DAST (Dynamic Application Security Testing) platform purpose-built for CI/CD workflows and dev-first API security.
Key Features:
- API-first: Deep support for REST, GraphQL, gRPC, SOAP.
- CI/CD Integration: GitHub, GitLab, Jenkins, Docker, Slack, Jira.
- Test-as-Code: Run security tests as part of your development cycle.
- Executive dashboards + dev-focused feedback.
Figures:
- $47.3M funding
Pricing:
- Pro: $49/user/month (min. 5 users).
- Enterprise: $59/user/month (min. 20 users).
- Custom quotes for large teams.
Visit StackHawk for more information.
Postman Security
Domains: Shift-Left Security & Developer Enablement
Differentiators: API governance, schema validation, IDE integration
Built into the most popular API development platform, Postman Security promotes shift-left practices by integrating testing, governance, and compliance directly into the developer experience.
Key Features:
- Policy Enforcement: Prevents non-compliant APIs from pre-deployment.
- Vulnerability Scanning: Catch misconfigurations during design.
- Centralized Governance: Versioned APIs with collaborative controls.
- CI/CD Ready: Works with GitHub, Jenkins, and all major IDEs.
Figures:
- 25M+ users globally across enterprises and startups.
Pricing:
- Free: Individual use.
- Basic: $14–$19/user/month.
- Professional: $29–$39/user/month.
- Enterprise: $49/user/month.
Visit Postman for more information.
Burp Suite (Professional)
Domains: Open Source Tools
Differentiators: Pen-testing standard, hybrid automation/manual testing
The gold standard for manual and semi-automated API penetration testing. Burp Suite is trusted by security professionals worldwide for its powerful suite of tools – Repeater, Intruder, Scanner, and Fuzzer.
Key Features:
- Manual + automated API testing with deep customization.
- Burp AI (2025): Smart assistant for noise reduction and workflow efficiency.
- 10,000 free AI credits with Pro edition (2025).
- Extensions through the BApp Store.
Figures:
- Used by over 70,000 professionals worldwide (2025).
Pricing:
- $449/year per user (Professional) (Source).
- Free Community Edition (limited features).
Visit Burp Suite for more information.
Coraza
Domains: Open Source Tools
Differentiators: Go-based ModSecurity alternative, CRS v4 support
Coraza is a high-performance, enterprise-grade open-source Web Application Firewall (WAF) built in Go for cloud-native environments. Positioned as a drop-in replacement for legacy ModSecurity engines, it offers full compatibility with the OWASP Core Rule Set (CRS) while being far more adaptable, efficient, and developer-friendly. It supports a wide range of deployment models, making it a go-to choice for modern API gateways, service meshes, and reverse proxies.
Key Differentiators:
- Go-Based Architecture: Lightweight and fast, built for low-latency inspection and scalable cloud-native use cases.
- ModSecurity Compatibility: Fully supports SecLang and CRS rules for seamless transition from older engines.
- Deployment Flexibility: Use it as a Go library, reverse proxy, standalone container, WASM plugin (Istio, Envoy), or middleware for Traefik, Caddy, and others.
- Programmable Security: Supports event hooks, plugins, and custom audit logging for tailored WAF behavior.
- Content-Aware Inspection: Inspects JSON, XML, multipart forms, and more – ideal for diverse modern workloads.
- Open Source Governance: Maintained by the OWASP Foundation with a transparent roadmap and active community development.
Figures:
- Launched in 2021
- Default WAF in several modern API gateway stacks
- Widely adopted for replacing ModSecurity in Kubernetes-native environments
- Active contributions from the global community and enterprise users
Pricing:
- Free and Open Source: Licensed under Apache 2.0 – no fees, limits, or hidden costs.
- Enterprise Support: No official paid version, but support and managed services may be available via third-party vendors.
Visit coraza.io for more information.
How API Security Tools Work
Understanding how API security tools function is key to choosing the right solution for your team. While the feature sets may vary, most tools fall into one or more of the following three categories:
API Discovery & Posture Management
These tools help you inventory every API in your ecosystem – including unmanaged, deprecated, and shadow APIs you may not even know exist. They analyze what each API exposes (such as PII, tokens, or sensitive business data) and assess the risk associated with each endpoint. This category answers the question:
“What APIs do we have, and where are we most exposed?”
Look for tools that:
- Automatically map APIs across cloud/on-prem/hybrid environments
- Detect sensitive data exposure.
- Highlight configuration drift or policy violations.
- Support schema conformance (e.g., OpenAPI validation)
Runtime API Protection
Once APIs are live, runtime protection kicks in. These tools act like real-time bodyguards – monitoring traffic for signs of abuse, bot activity, or zero-day exploits. Advanced platforms use AI/ML to baseline normal behavior and block anomalies before damage is done.
They typically:
- Monitor live traffic across all environments
- Block malicious requests, brute-force attempts, and business logic abuse
- Integrate with SIEM, SOAR, and DevOps tooling.
- Offer inline or out-of-band deployment for minimal latency
Some even visualize attacker behavior as it unfolds – so you can trace the kill chain and respond faster.
API Security Testing (Shift-Left)
Security doesn’t have to wait for deployment. Tools in this category allow you to embed security directly into the development pipeline (a concept known as shift-left). These solutions help devs find and fix issues before they hit production.
Capabilities often include:
- Static and dynamic API scanning (SAST, DAST)
- Security linting and schema enforcement
- CI/CD integrations (e.g., GitHub Actions, Jenkins, Azure DevOps)
- Governance policy checks and test-as-code
Testing tools are essential if your organization practices DevSecOps or manages frequent API deployments.
Combining Forces
Leading platforms – like AppSentinels, Salt, and Traceable – blend all three layers: posture management, runtime protection, and security testing. That means your APIs are covered before, during, and after they’re deployed.
Depending on your use case, a tool might lean more toward one category than another, but the best ones help teams bridge development and operations without friction.
Use Case Matrix
With so many players in the API security space, it’s easy to get overwhelmed by the feature checklists. Instead of ranking by popularity, we’ve mapped tools based on where they excel in real-world use cases.
Many tools offer overlapping functionality, but this matrix highlights where each platform delivers its strongest value – from enterprise-ready defense to shift-left developer workflows and advanced runtime analytics.
Use Case / Capability | Best-Fit Tools |
Full Lifecycle API Security | ✓ AppSentinels, ✓ Salt Security, ✓ Traceable AI, ✓ Akamai (Noname Security), ✓ Firetail |
Business Logic Protection & Advanced Defense | ✓ AppSentinels Limited scope: ✓ Cequence Security, ✓ Traceable AI, ✓ Wallarm, ✓ Firetail, ✓APIsec |
Shift-Left Security & CI/CD Integration | Fully automated: ✓ AppSentinels, ✓ Escape, ✓ APIsec Test engineers manually author and manage cases: ✓ 42Crunch, ✓ Postman Security, ✓ StackHawk |
Runtime Threat Detection & API Analytics | ✓ AppSentinels, ✓ Traceable AI, ✓ Cequence Security, ✓ Wallarm, ✓ Akamai, ✓ Firetail |
Shadow / Zombie API Discovery | ✓ AppSentinels, ✓ Akamai (Noname Security), ✓ Traceable AI, ✓ Firetail |
LLM / GenAI API Discovery / Protection | ✓ AppSentinels ✓ Traceable AI, ✓ Imperva |
Bot Mitigation & Fraud Prevention | ✓ AppSentinels, ✓ Cequence Security, ✓ Wallarm, ✓ Firetail |
Manual API Pen-testing | ✓ Burp Suite Pro |
Open Source Security Stack | ✓ Coraza, ✓ Burp Suite (Community) |
High-Compliance / Regulated Environments | ✓ AppSentinels, ✓ Imperva, ✓ CloudGuard, ✓ Salt Security, ✓ Firetail |
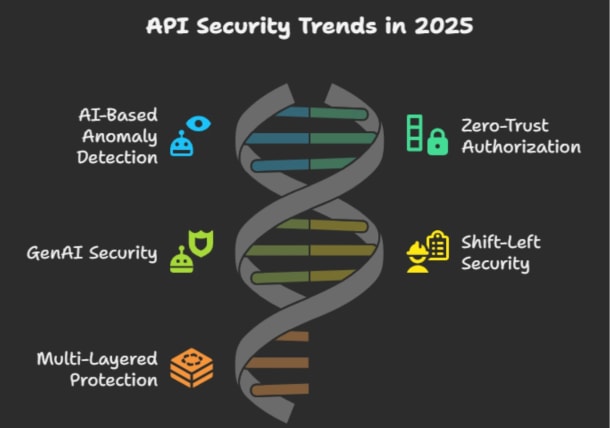
Trends Shaping API Security in 2025
API security in 2025 is evolving rapidly. With LLMs flooding endpoints, apps becoming modular and distributed, and attackers focusing on abuse over exploits – security teams must rethink how they monitor, test, and protect APIs across environments.
Below are the five biggest shifts defining the API security space today:
AI-Powered Observability & Behavior-Based Detection
As traffic volume and application complexity grow, traditional WAF signatures and static rules can’t keep up. That’s where AI-based anomaly detection steps in.
- Modern tools baseline API behavior, detect subtle anomalies, and flag behavioral deviations that static scans often miss.
- Especially effective for catching low-and-slow attacks, abuse of intended workflows, and bot-driven reconnaissance.
- Seen in: AppSentinels, Cequence, Rakuten SixthSense, Akamai.
AI-driven analytics are becoming table stakes – not just for attack detection, but for visibility, policy automation, and incident response.
Zero-Trust & Fine-Grained Authorization Becomes Mandatory
With APIs now powering critical functions and sensitive data, Zero Trust principles are foundational to securing traffic.
- Tools are integrating Open Policy Agent (OPA), OAuth 2.1, and JWT validation for contextual, identity-aware access control.
- Every API call must be evaluated, logged, and governed, especially for regulated sectors like healthcare, fintech, and infra.
- Adopted by: AppSentinels, Akamai, Curity, API7.
Authorization failures like BOLA remain the #1 API risk. Moving from “permissioned” to “policy-verified” is how teams stay safe.
GenAI Is the New API Attack Surface
LLMs and GenAI tools don’t just use APIs – they expose new vulnerabilities through them:
- Attackers exploit APIs connected to GenAI agents through prompt injection, model hijacking, and information leakage.
- APIs must be hardened not only against traditional threats but against model misuse and untrusted input.
- Seen in: AppSentinels, Traceable AI, Imperva, Thales.
As AI agents become more autonomous, API boundaries blur, and security must evolve to keep control.
Shift-Left Security Is Now Real (and Critical)
“Shift left” is no longer a buzzword – modern API security starts in development:
- Tools now offer automated API scans, OpenAPI linting, contract enforcement, and security gates inside CI/CD.
- By catching vulnerabilities during design or testing, teams reduce production risks and developer rework.
- Pioneered by: AppSentinels, 42Crunch, StackHawk, Akto, APIsec.
The next wave of breaches won’t come from missed patches, but from insecure-by-design APIs. Shift-left makes prevention scalable.
Multi-Layered Protection Across Clouds, Environments, and APIs
Most breaches don’t come from the main APIs – they come from shadow, zombie, or misunderstood ones.
- Leading platforms now offer multi-layered defense-in-depth: from discovery and testing to runtime blocking, bot protection, and BOLA-aware enforcement.
- Visibility across cloud-native, hybrid, and legacy environments is a must.
- Leaders here: AppSentinels, Salt, Traceable.
APIs no longer live in one place. Protection must move with them.
Wrapping Up: There’s No One-Size-Fits-All API Security Tool
The best API security tool isn’t the flashiest – it’s the one that fits your stack, your risks, and your team. Whether you need full lifecycle coverage, deep developer integrations, or open-source flexibility, there’s a solution in this list built for you.
Start by mapping your API exposure. Know where your risks lie. Then pick the tool (or combo) that strengthens your posture without slowing you down.
API security isn’t optional in 2025. It’s fundamental.