The Invisible Arteries of the Internet
Every tap, swipe, and sync you make online is powered by an API.
When you pay through GPay, check your Uber ride status, or stream music on Spotify, a quiet exchange takes place between systems that don’t even belong to the same company. These invisible connections are what make modern life seamless.
But the same bridges that move data across clouds are beginning to crack. APIs now account for over 80% of all web traffic, and attacks targeting them have surged by more than 30% in the past year alone. Each incident may start small – a misconfigured endpoint, a leaked key – but the fallout can cascade across entire ecosystems.
APIs are the most critical and least visible part of our digital infrastructure. They keep every business, service, and transaction running, yet when they fail, they can silently disconnect millions. A simple Instagram story linking to your Spotify playlist might look effortless, but behind that magic lies a fragile exchange of tokens, requests, and data – all depending on trust.
APIs are the digital bridges that let apps talk to each other, but those same bridges have become one of the biggest attack surfaces on the internet.
These invisible arteries power the internet. The question is: How many of them should we expose, and to whom?
What an External API Really Is (and Why It Matters)
At its simplest, an external API is a door.
It lets third-party developers or partner applications access specific data or functionality, securely and in a controlled way. Think of it like a restaurant menu: you can place an order, but you don’t get to walk into the kitchen.
You interact with external APIs every day:
- Google Maps API powers maps inside delivery and travel apps.
- Stripe API enables smooth online payments.
- OpenAI API brings chatbots and AI assistants to life.
- Plaid API connects fintech apps to your bank account.
To keep these interactions safe, most systems use an API gateway – the front door that checks credentials, controls request limits and decides where data can go. Gateways such as AWS API Gateway, Kong, and Azure API Management handle authentication, routing, and basic validation, keeping backend services hidden behind protective layers.
Security Tip: Always route external requests through an API gateway with authentication and logging enabled. Never expose backend endpoints directly.
While REST remains the most common format, GraphQL external APIs are gaining traction for their flexibility. They allow clients to fetch only the data they need, reducing network load but also introducing new security challenges related to query control and data exposure.
External APIs enable innovation, but each new connection also expands the attack surface. Understanding that balance is where modern API security truly begins.
Internal, Partner, and External APIs: Where the Walls Get Thinner
Not all APIs are created equal. The moment an interface moves from inside your network to the outside world, the risk multiplies.
Think of three concentric circles: internal, partner, and external – each expanding the surface area of trust, access, and exposure.
Internal APIs: The Hidden Backbone
These quietly connect your own systems: syncing inventory, processing reports, or linking microservices. Even behind firewalls, undocumented endpoints (shadow APIs) can leak sensitive data.
Rule of thumb: Treat internal APIs as you would external ones. Track every endpoint, manage versions, and maintain visibility. Check out our API Audit Checklist to learn more.
Partner APIs: The Trusted Bridges
Partner APIs connect you to clients, vendors, or service providers. They’re how collaboration happens without handing over full backend access.
For example, Plaid’s Link Account API lets a budgeting app access verified bank data without seeing your credentials. Even with strong authentication, misconfigurations or changes in your partner’s system can create risks.
External APIs: The Public Gateways
External APIs are fully open to developers, partners, and the public. They transform products into platforms, powering ecosystems like Stripe, Google Maps, and Spotify.
But openness has a cost. Every exposed endpoint is a potential entry point to sensitive data or business logic.
As the line goes:
“Most breaches don’t come from zero-days. They come from exposed APIs no one was watching.”
Here’s how the risk grows across API types:
| API Type | Typical Use | Security Posture | Common Risk | Governance Need |
| Internal | Inside the org (e.g., warehouse → website sync) | Low visibility | Shadow APIs, no version control | Ownership & monitoring |
| Partner | Shared with vendors/clients | Moderate | Misconfigured scopes, dependency failures | Policy & scope management |
| External | Public-facing APIs | High exposure | Data leaks, abuse, and credential attacks | Continuous runtime protection |
In short:
- Internal APIs drive efficiency.
- Partner APIs enable collaboration.
- External APIs unlock innovation and risk. (The ones we are going to learn more about)
The thinner the boundary, the stronger your governance must be.
Why Companies Still Open Their APIs to the World
If open APIs are risky, why do companies keep building them?
Because they’re also the fastest way to innovate, scale, and grow, opening an API isn’t just a technical choice. It’s a strategic advantage.
Innovation at Scale
APIs invite external developers to build what your team can’t.
Slack’s open API ecosystem turned a team chat tool into a global productivity platform, now home to over 2,000+ integrations built by the community.
Revenue Through the Backend
For some, APIs are the business model.
Twilio’s per-message API pricing built a billion-dollar communications platform.
Stripe did the same with payments: every API call is a revenue unit, replicated millions of times a day.
Ecosystem Growth
Open APIs multiply your reach.
Spotify’s developer APIs have enabled over 100,000 integrations, ranging from playlist curators to analytics dashboards.
Salesforce’s AppExchange runs entirely on its open APIs, powering an entire marketplace of third-party apps.
Speed and Scalability
Composability replaces months of engineering with days of integration.
A travel startup today can launch globally by stitching together:
- Flights: via Skyscanner APIs
- Maps: via Google Maps APIs
- Payments: via Stripe APIs
What once took months now takes minutes, powered by reusable APIs.
The Data Flywheel
Every API call creates behavioral data – fuel for analytics, personalization, and AI models.
API-first companies achieve faster partner integrations and much shorter go-to-market cycles than traditional setups. By 2025, over 80% of new digital innovations will involve at least one exposed API.
The Catch
Every open API expands your perimeter of trust. Each connection, integration, or webhook is one more potential attack surface.
Being open isn’t the challenge anymore.
Being open safely is.
The Hidden Risks Behind External APIs
The same APIs that power innovation can quietly become your most significant security risk.
From 2024 to 2026, external API breaches were among the fastest-growing causes of data exposure, accounting for more than half of all major application-layer incidents worldwide.
When APIs move outside your trusted perimeter, they don’t just exchange data. They exchange control.
Top External API Risks (Explained)
1. Broken Authentication
Weak or reused tokens, misconfigured OAuth flows, or missing session checks can allow attackers to impersonate users or services.
Example: A misconfigured authentication endpoint exposed millions of user records in a 2022 Twitter incident.
2. Data Exposure
APIs sometimes reveal more than they should – internal IDs, configuration metadata, or complete customer profiles.
Example: T-Mobile’s 2021 breach exploited exposed API fields, leaking 54 million customer records.
3. Mass Enumeration
If rate-limits and pagination aren’t enforced, APIs can be scraped at an industrial scale.
Example: LinkedIn’s API was used to harvest 700 million user profiles in 2021.
4. Shadow APIs
Undocumented or forgotten endpoints, often left over from testing, expose sensitive data.
Poor API discovery and visibility remain among the leading causes of modern breaches.
5. Business Logic Abuse
Attackers no longer need injections; they exploit logic itself.
By chaining legitimate endpoints, they trigger unintended actions, such as coupon fraud, reward drains, or transaction bypasses.
Broken Object Level Authorization (BOLA) also remains among the most common and dangerous API vulnerabilities, accounting for a significant share of real-world attacks.
Want to learn more about this? Read:
- API Business Logic: What & Why they exist & how to protect
- Business Logic Vulnerabilities Explained: Real Examples, Impact & How to Prevent Them
6. Over-Permissive Keys
One leaked key with “admin” scope can undo every security layer.
GitHub and CI/CD leaks are rampant, and the 2025 xAI incident exposed keys linked to 50+ AI models across government systems.
All these breaches reveal a more profound truth: APIs are no longer behind your firewall. They are your firewall.
Every new endpoint, partnership, or integration expands your attack surface. The latest challenge isn’t closing APIs off, it’s keeping them open safely.
How External APIs Actually Work (and Why That’s the Problem)
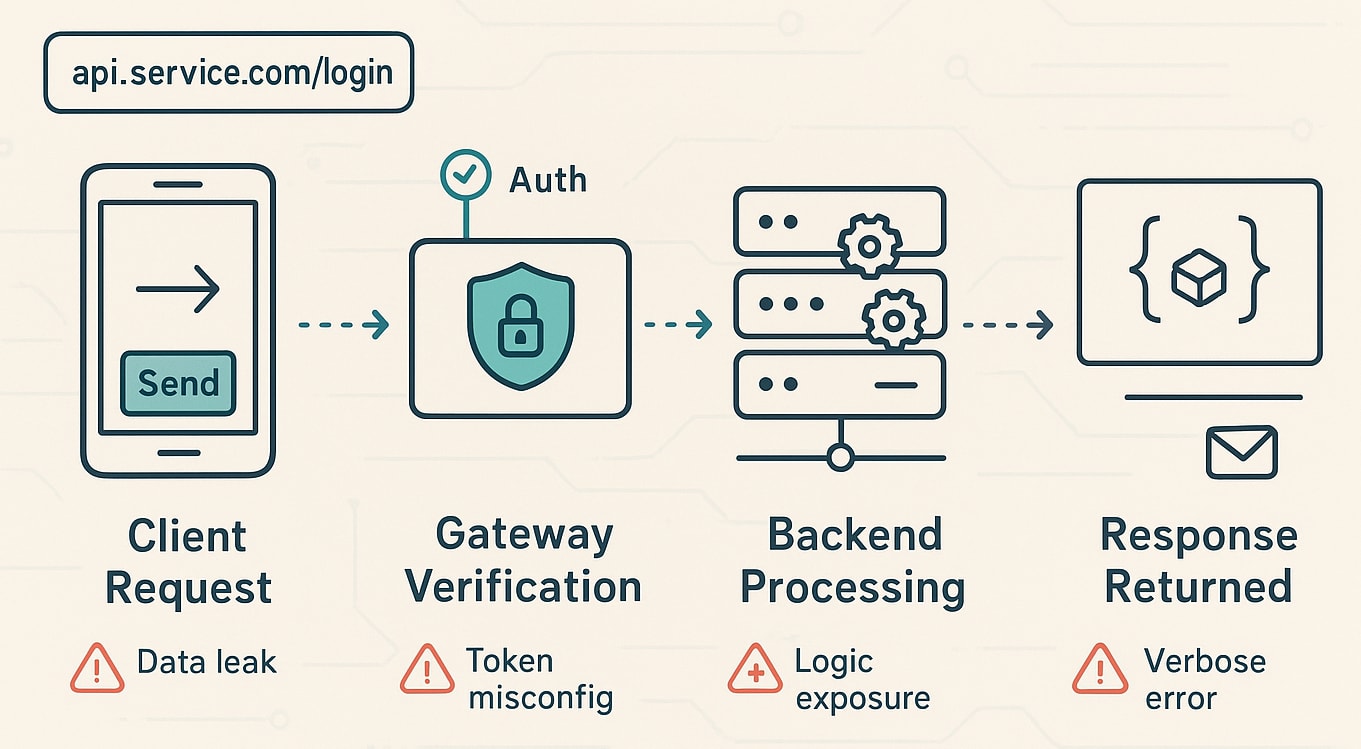
Understanding how an API request travels helps explain why things so often go wrong.
The Journey of a Single API Call
- Client Request: A user or app sends a request like api.service.com/login.
- Gateway Verification: The API gateway checks identity, tokens, and rate limits.
- Backend Processing: Internal logic fetches or updates data.
- Response Returned: A structured JSON payload is sent back.
At each step, one missed validation or verbose error can leak sensitive data, authentication flows, or even business logic.
Where Vulnerabilities Hide
1. Weather App Key Exposure
A developer leaves a live API key inside the response metadata.
Impact: Anyone viewing network traffic can copy and reuse that key for unlimited access.
Mitigation: Scrub headers, mask secrets, and rotate compromised tokens immediately.
2. E-Commerce Price Manipulation
Endpoint: /price?productID=123&discount=30
Impact: Attackers modify parameters to change discounts or bypass pricing rules.
Mitigation: Validate parameters on the server side and enforce canonical pricing.
Developer Snapshot
| // Simple fetch external API call |
Even this three-line snippet can leak secrets if copied into public code or if CORS policies are too broad.
API Calls Inside Containers
Modern apps often call external APIs from within Docker containers or microservices.
If outbound egress rules aren’t locked down, a single compromised container can expose credentials across the entire environment.
Best Practice: Use per-service credentials and enforce outbound network segmentation.
The Bigger Insight
APIs leak more than data. They leak behavior.
Endpoint patterns, query parameters, and timing all reveal how your system thinks. Attackers don’t just look for data dumps; they learn your business logic and weaponize it.
The API economy thrives on openness, yet that same openness has outpaced traditional security controls.
Next, we’ll explore how this imbalance created today’s most prominent blind spot, and how AppSentinels is redefining what it means to secure an API in real time.
Also read:
The Rise of the API Economy (& Why Security Lagged Behind)
The 2020s brought a seismic shift: products became platforms. Companies now expose their core capabilities via APIs, enabling third-party developers to innovate, integrate, and monetize faster than ever.
APIs are no longer features. They are the backbone of digital business.
- By 2027, APIs are projected to generate $14.2 trillion in global economic impact, exceeding the combined GDP of the UK, Japan, France, and Australia.
- 43% of API-first organizations already derive over 25% of their revenue directly from APIs (Postman, 2025).
Yet security hasn’t kept pace. Many organizations still track APIs in spreadsheets, lack real-time runtime visibility, and rely solely on gateway logs. The result: shadow APIs, undocumented endpoints, and unnoticed business logic flaws create blind spots for attackers.
“You can’t protect what you can’t see.”
This gap created an urgent demand for real-time visibility solutions. We have designed our platforms precisely for this.
Securing External APIs with AppSentinels
Turning API chaos into clear, continuous visibility.
APIs are everywhere – internal, partner, external. Managing them all can feel impossible. AppSentinels makes it simple, giving organizations control across the entire lifecycle, from development to production.
- Find everything, automatically: Live APIs, shadow APIs, unused or orphan endpoints, even LLM-powered APIs – nothing hides.
- Test like a full-time security team: Continuously checks workflows and business logic, spotting weak spots before attackers do.
- Stop attacks in real time: Detects abuse, injections, and logic attacks as they happen, blocking threats automatically.
- Prioritize what matters: Real traffic and business impact guide risk scoring, no more wasting time on low-priority alerts.
- Fits right into your stack: Works with CI/CD pipelines, ticketing tools, and API gateways like Jenkins, GitHub Actions, Kong, AWS, and Apigee.
- Built for scale: Secures 100B+ API calls monthly for BFSI, fintech, retail, and SaaS clients. Cloud, on-prem, or hybrid – AppSentinels grows with you.
- Trusted and recognized: Named a Leader in the 2025 GigaOm Radar for API Security. We were one of the closest platforms to the bullseye.
Get the full GigaOm Radar report here.
With AppSentinels, real-time visibility, automated protection, and future-ready defenses, organizations can keep APIs open safely, enabling innovation to thrive without compromise.
How to Use an External API (Safely)
Opening APIs comes with responsibility. Developers don’t just integrate functionality. They also protect data, maintain reliability, and ensure secure operations. Here’s a practical framework for safely connecting to external APIs.
Developer Checklist
Follow these core practices to protect your API integrations:
- Rotate and encrypt API keys regularly.
- Enforce rate limits and granular access scopes.
- Log and monitor all traffic to detect anomalies.
- Mask or omit sensitive fields in responses.
- Validate request and response schemas to prevent abuse.
- Continuously monitor for unusual activity, especially on external-facing endpoints.
Tip: “Even if you trust your providers, verify continuously.”
Code Examples
Here are simple ways to call an external API safely across popular tech stacks:
Spring Boot (Java)
| RestTemplate restTemplate = new RestTemplate(); |
Next.js (Node.js/React)
| export async function getServerSideProps() { |
AWS Lambda (Python)
| import requests |
Laravel (PHP)
| $response = Http::get(‘https://api.example.com/data’); |
Django (Python)
| import requests |
Salesforce (Apex)
| HttpRequest req = new HttpRequest(); |
No-Code / Low-Code Platforms
Bubble, Webflow, Adalo, AppSheet – use built-in API connectors or custom actions. Authenticate securely, test with sample payloads, and limit permissions.
Test and Protect Your Integrations
Even the best-written code can fail if the API misbehaves. Use these strategies to build resilient integrations:
Mocking Strategies
- Simulate real API behavior with fake endpoints or responses.
- Allows frontend and backend development to proceed in parallel.
- Helps test edge cases, success/failure scenarios, and timeouts.
- Integrate mocks into unit tests and CI pipelines.
Timeout Handling
- Timeouts prevent apps from hanging when slow API responses occur.
- Test by simulating delayed or dropped connections.
- Set realistic timeouts, implement retries with exponential backoff, and provide user feedback (loading spinners and error messages).
Circuit Breakers
- Prevent repeated calls to failing APIs and avoid cascading failures.
- If an API fails repeatedly, the circuit “opens” to block requests, then closes after recovery.
- Combine with timeouts and retries for robust error handling.
Platform-Specific Integration
Different platforms have their own quirks. Here’s a concise guide to safely connect external APIs:
No-Code / Low-Code
- Bubble: API Connector plugin; authenticate via API key or OAuth; test with mock data; use server-side actions for security.
- Webflow: Embed JS using fetch or XMLHttpRequest; use environment variables; validate responses.
- Adalo: Custom Actions with authentication; simulate errors; limit permissions.
- AppSheet: Webhook/API integration; test payloads; ensure HTTPS and authentication.
Data & Analytics
- Airtable: REST API with keys; respect rate limits; batch requests; rotate keys regularly.
- Snowflake: External functions/connectors; OAuth/key-pair auth; role-based access; audit logs.
ERP / CRM / Vertical Platforms
- Odoo: JSON-RPC/XML-RPC; authenticate with credentials/tokens; monitor logs; enforce IP/password policies.
- ADP / AlayaCare: OAuth/SAML; PHI and consent compliance; audit API activity.
Business & Marketing Automation
- Adobe Campaign Standard: Trigger campaigns or sync data with OAuth; test in the sandbox first.
- External Approval APIs (Supplier Management): Automate workflows, use scopes and audit logs, and regularly review permissions.
Pro Tip: Always enforce authentication, rate limiting, and input validation, and pair with real-time monitoring for anomaly detection.
Safe external APIs aren’t just about protecting data. They’re about trust, reliability, and preserving your business logic. Even minor oversights – hardcoded keys, unvalidated responses, or open CORS policies – can put your app and your users at risk. Build in security, test often, and monitor continuously.
The Future of External APIs: From Open Doors to Intelligent Gateways
APIs are no longer just endpoints for exchanging data. They’re evolving into autonomous ecosystems powering AI agents, bots, and next-gen digital experiences. The days of static, open endpoints are ending, replaced by intelligent, adaptive gateways that actively defend themselves.
What’s Next for APIs
- Self-Defending APIs: Endpoints automatically detect abuse patterns, anomalous behavior, and malicious payloads.
- Zero-Trust Per-Call Authentication: Every request is verified, contextualized, and authorized, with no implicit trust.
- Unified Observability: Real-time monitoring across all endpoints, partners, and external services, giving teams actionable intelligence on traffic, usage, and risk.
The future of API security lies in protection through intelligence, not closure. Open doors will remain, but they’ll be more intelligent, adaptive, and self-guarded – enabling innovation without compromise.
Quick Recap
Here’s everything you need to remember in half a minute:
- APIs are the backbone of modern digital business, but growth has outpaced security.
- Real-time visibility and runtime protection are critical for preventing data leaks, business logic abuse, and shadow endpoints.
- Use developer best practices: rotate keys, validate schemas, monitor traffic, and test resilience.
- Platform-specific guidance ensures safe, efficient integration.
- The future is autonomous, self-defending APIs, powered by intelligent gateways and zero-trust security.
FAQs: Top External API Questions
How do external APIs impact app reliability?
Unstable or slow APIs can break workflows, delay responses, and increase error rates. Monitoring, retries, and fallback logic help maintain app stability.
Can external APIs be safely used in no-code platforms?
Yes. With secure connectors, server-side authentication, and thorough testing of payloads and edge cases before going live.
Do external APIs comply with data privacy regulations?
They can be, if encrypted, authenticated, logged, and appropriately audited in accordance with GDPR, HIPAA, or local rules. Always verify provider compliance.
What are the hidden costs of using external APIs?
Excessive requests, rate-limit breaches, retries, and error handling can increase compute usage and latency, affecting both performance and billing.
How do external APIs handle authentication securely?
Through API keys, OAuth tokens, or certificate-based methods. Rotate keys, limit scopes, and avoid embedding secrets in client-side code.
How can businesses track usage and prevent abuse?
Use real-time logging, anomaly detection, and API security platforms to monitor patterns, detect credential leaks, and enforce rate limits.
What happens if an external API changes unexpectedly?
Breaking changes can disrupt workflows. Use versioned endpoints, automated schema validation, and CI/CD checks to catch issues early.
Conclusion: APIs Built the Modern Web. Security Will Keep It Standing.
External APIs aren’t just technical tools. They’re building blocks for your projects, apps, and integrations. Used thoughtfully, they let you pull in data, automate workflows, and connect with platforms in ways that used to take weeks or months.
But openness comes with responsibility. Every key, endpoint, and integration expands your attack surface, so you need visibility, validation, and protection baked in. When you pair smart usage with strong security practices, APIs become enablers, not risks.
So go ahead – try external APIs in your next project. Connect, experiment, and innovate. Just make sure you’re doing it safely and responsibly.