
OWASP API Top 10 2023: What changed and why it’s important?
Back in 2019, OWASP released its first API Top-10 list. It quickly gained widespread acceptance and acknowledgment from the industry about the challenges faced in protecting APIs. Since then, growth in APIs has continued, and the threat landscape also evolved rapidly. OWASP has released an updated API Top 10 2023 with quite a few changes from 2019 to address the changes and provide new insights and recommendations. Let’s take a closer look at these changes to understand how they impact us:
Differences
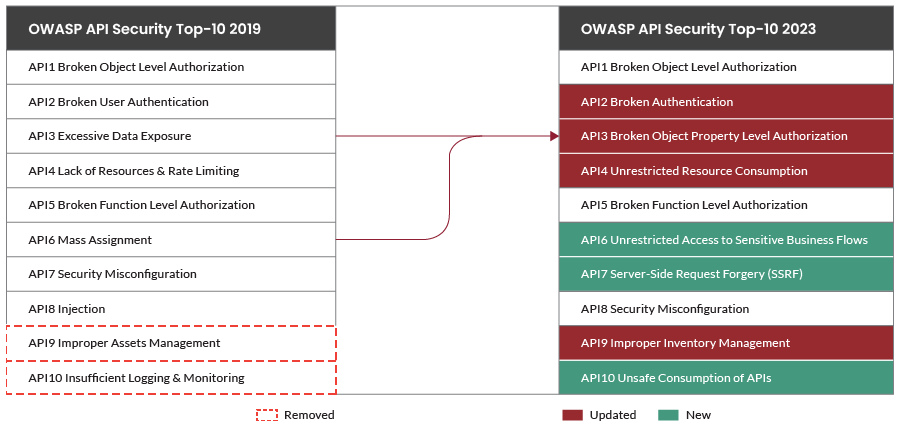
Here are the differences between OWASP API Top-10 2023 and OWASP API Top-10 2019:
Unchanged Categories
Broken Object Level Authorization (BOLA), Broken Function Level Authorization (BFLA), and Security Misconfigurations are three unchanged OWASP Top 10 API vulnerability categories in the 2023 list. BOLA and BFLA’s positions remain unchanged, while Security Misconfigurations’ position decreased by one place.
BOLA remains a go-to attack vector for malicious users and remains in the #1 position as fine-grained Object-level authorization mechanisms are complex and challenging to implement.
Excessive data exposure
Looking forward to generic implementations, developers expose all object properties without considering their sensitivity, relying on clients to filter data before displaying it to the user.
BFLA and security misconfigurations remain unchanged in their rankings because they are still trendy, easily exploitable, and have vast implications.
New Additions
The 2023 list includes new additions: Unrestricted Access to Sensitive Business Flows at the #6 position, Server-Side Request Forgery (SSRF) at the #7 position, and Unsafe Consumption of APIs at the #10 position.
The unrestricted access to the Sensitive Business Flows category comprises threats that can be mitigated by implementing rate-limiting measures.
SSRF, also in the OWASP Web Top 10 list, has entered the API Top 10 list. SSRF attacks have significantly increased over the years as many developers build application workflows that access external resources via URLs like webhooks, SSOs, files, etc., for flexibility and ease of use. SSRF vulnerabilities are dangerous, standard, and difficult to mitigate.
Updated Categories
Complex access control policies with different hierarchies, groups, and roles and an unclear separation between administrative and regular functions tend to lead to authorization flaws. By exploiting these issues, attackers access other users’ resources and/or administrative functions.
Mass assignment
Broken User Authentication is updated to Broken Authentication and retains the #2 position on the list. This expands the category beyond user-level authentication into service authentication as well, opening risks beyond user-authentication flaws like weak or missing authentication across micro-services.
Broken Object Property Level Authorization, ranked #3, combines Excessive Data Expose (API03:2019) and Mass Assignment (API06:2019). The new name emphasizes the need to focus even more on fine-grained authorization in the application. It’s even more critical for GraphQL, like flexible query languages where an attacker has to add an already known parameter to illegally access or modify it.
Lack of Resources and Rate Limiting (API04:2019) has been renamed to Unrestricted Resource Consumption. Previously, the focus was only on vulnerabilities, but now it expands the horizon and highlights the consequences of not having proper rate limits and other restrictions on resource usage. Other limitations, such as execution timeouts, maximum memory, or number of processes, are also included. Together, these limits help ensure the proper functioning of the APIs.
Improper Asset Management (API09:2019) has been renamed Improper Inventory Management and retains the #9 position in the list. This change clarifies the importance of maintaining an up-to-date inventory of APIs and the sensitive data they expose as organizations rapidly change their applications.
The Categories That Were Removed
Insufficient Logging and Monitoring (API10:2019) and Injections (API0:2019) have been removed from the list. While API-based applications may still be exposed to generic security risks like injections (SQLi, RCE, XSS), OWASP API’s Top 10 objective emphasizes special attention to risks relevant to APIs.
Summary & Take-Away
Fine-grained authorization remains the most significant risk to API security, with three of the Top Five categories attributed to it—BOLA, BOPLA, and BFLA. These flaws require security platforms to build a deep understanding of application behavior. It is important to note that these flaws can be addressed mainly during the development cycle by a correct Shift-Left initiative.
Almost equally important is the need to ensure proper usage of APIs or protection against unrestricted and unsafe consumption of APIs. As APIs simplify application development, they similarly help malicious users develop attacks on applications. Many of these techniques are deployed by malicious users to run at scale. Here comes the importance of Protect-Right for APIs.
The rest of the categories are generic regarding hygiene and inventory management.
About AppSentinels
AppSentinels has built the world’s most comprehensive full-life-cycle API Security Platform. Its deep learning models discover missing fine-grained authorization flows in the application and enforce them, protecting applications from breaches, data loss, and fraud. Its platform has Shift-Left and Protect-Right capabilities and provides Continuous API Discovery, Continuous Stateful API-DAST (testing), Run-time Protection, and Remediation. Some of the most prominent names in the industry are engaged with AppSentinels to protect their APIs. Talk to AppSentinels to discover the unknown about your APIs.
OWASP API Top 10 2023: What changed and why it’s important?
OWASP API Top 10 2023:
What changed and why it’s important?
Attend the webinar to learn about,
- What changed between the 2019 and 2023 OWASP’s top 10 list?
- How it impacts and changes to be made in our security?
- What action should CSO take immediately and in the long term?
- Why is OWASP’s 2023 top 10 list essential?

