Two Gatekeepers, One Confusing Debate
Walk into any security or platform team meeting, and eventually someone will ask: “Wait, what’s the actual difference between a WAF and an API Gateway?”
It’s not a dumb question. It’s an honest one.
After all, both sit at the edge. Both inspect HTTP streams. Both promise “security”. And if you read the marketing brochures, you might think they’re just two different names for the same wall.
But that’s where the confusion begins. Because while these two guards may stand shoulder-to-shoulder, they’re watching for entirely different things.
A Web Application Firewall (WAF) is your gate scanner, inspecting every incoming request for hidden weapons: SQL injections, XSS payloads, or anything matching OWASP‘s top threats. It doesn’t care why a request is coming; it only cares whether it looks dangerous.
An API Gateway, on the other hand, is more like air traffic control, managing how legitimate requests flow between clients and backend services. It decides who gets clearance (authentication), how often (rate limiting), and which route to take (routing, versioning). Its job isn’t to spot malware. It’s to keep the API skies organized.
If your API ecosystem were an airport:
- The WAF scans passengers at security, searching for weapons.
- The API Gateway coordinates flights, making sure each plane lands and takes off on time.
Both are critical. Both see the same traffic. Yet confusing them, or worse, depending on just one, creates blind spots where modern API threats thrive.
Because in 2026, the question isn’t which wall you use.
It’s what visibility lives between them.
WAF vs API Gateway: The Clear Breakdown
After years of blurred marketing and overlapping features, it’s easy to see why “WAF vs API Gateway” feels like a single product category. Both inspect traffic. Both promise to “secure APIs”.
But in reality, they solve two completely different problems: one protects, the other organizes.
Let’s separate their missions once and for all.
What Is a Web Application Firewall (WAF)?
A Web Application Firewall (WAF) is a specialized firewall that protects your web applications and APIs from malicious input. It operates 
Think of it as a digital security checkpoint. It scans each incoming passenger (request), looking for suspicious payloads – like SQL injections, cross-site scripting (XSS), or remote code execution attempts – all part of the OWASP Top 10.
How It Works
WAFs rely on:
- Rule sets and signatures that define known attack patterns (like regex for SQLi strings or JavaScript injection snippets).
- Anomaly detection systems that learn what “normal” traffic looks like and flag anything that deviates from it.
- Inline or reverse-proxy deployment, often through CDNs, to filter traffic before it reaches your app.
- Logging and alerting, giving security teams visibility into what was blocked, what passed, and what might be evolving.
Common examples include AWS WAF, Cloudflare WAF, and Azure Application Gateway (in WAF mode).
The Catch
But here’s the limitation:
A WAF doesn’t understand intent. It understands syntax.
It can tell you that a payload contains a suspicious “DROP TABLE” statement, but it can’t tell you whether a valid user is abusing their access token to scrape sensitive data.
WAFs were built for web apps, not for today’s sprawling API ecosystems. They can inspect a POST request body, but they often struggle with nested JSON, GraphQL queries, or chained API calls.
They also require continuous tuning to reduce false positives – a balance between catching real threats and not blocking legitimate traffic.
Or as we would put it:
“A WAF can stop a malicious injection, but not an authenticated user misusing a valid token.”
Want to explore options? Check out “Top 25 Web Application Firewalls (WAFs) of 2026: Cloudflare Alternatives, Features & Pricing”.
What Is an API Gateway?
If the WAF is the security scanner, the API Gateway is the air traffic control tower.
It’s not focused on stopping malicious payloads. It’s making sure every flight (API call) lands safely, takes off on schedule, and follows the correct route.
An API Gateway sits between clients and backend services, managing all API interactions. Its mission is to make APIs accessible, reliable, and governed.
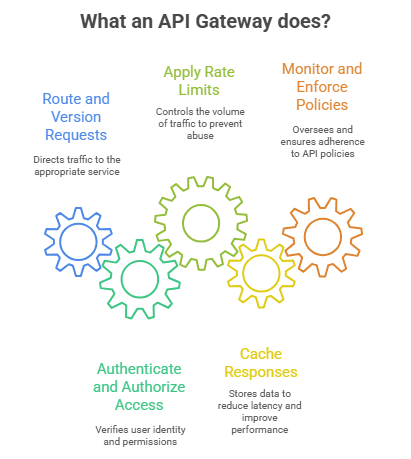
What It Does
An API Gateway:
- Routes and versions requests, ensuring each service gets the right traffic.
- Authenticates and authorizes access using protocols such as OAuth 2.0 or JWT tokens.
- Applies rate limits to prevent excessive or abusive traffic.
- Caches responses to reduce latency and improve performance.
- Monitors and enforces policies across distributed APIs.
Tools like AWS API Gateway, Azure API Management, Kong, and Apigee dominate this space.
What It Doesn’t Do
Here’s where confusion sets in – an API Gateway secures access, not behavior.
It can verify that a user has a valid token, but it cannot verify what they do with it.
It can throttle requests per minute, but cannot detect whether those requests contain payloads intended to exfiltrate sensitive data. And because DevOps or platform teams often manage API Gateways, while WAFs belong to AppSec, the two systems rarely share logs or visibility into each other.
So even though both watch the same traffic, one is blind to payloads, while the other is blind to intent.
Or as the metaphor goes:
“A Gateway ensures only valid passengers board, but doesn’t know who’s smuggling contraband in plain sight.”
Want to explore options? Check out “The 15 Best API Security Tools in 2026 – Ranked by What They Do”.
WAF vs API Gateway: The Real Differences
Let’s strip the jargon and see how they truly diverge in purpose and capability.
Aspect | WAF | API Gateway |
Core Mission | Protect apps from malicious payloads | Manage, route, and authenticate API traffic |
Primary Focus | Security enforcement | Access and orchestration |
Understands | Payloads, parameters | Endpoints, users |
Protects Against | Code injection, XSS, bot traffic | Abuse, throttling, and auth misconfigurations |
Data Type | HTML, form-data, JSON | JSON, XML |
Visibility | Syntactic (request-level) | Functional (endpoint-level) |
Ownership | SecOps / AppSec | DevOps / Platform |
Failure Mode | Missed payloads, false positives | Policy drift, excessive exposure |
Both serve vital but complementary roles. The WAF is a security tool that treats from the stream. The API Gateway is an orchestration tool: it structures how that stream flows.
But when they operate in isolation, each inherits the other’s blind spots:
- The WAF blocks the obvious attacks but misses token abuse or excessive API exposure.
- The Gateway enforces policies but misses subtle payload manipulations.
In modern distributed systems, these gaps are where attackers live – exploiting the space between detection and control.
That’s why in 2026, the most innovative teams don’t debate “WAF or API Gateway”. They ask: How do we connect what each sees?
Or, as we like to put it:
“Both watch the same traffic. One hunts anomalies, the other enforces order.”
Why Teams Confuse Them
If your team has ever debated whether the WAF or the API Gateway “covers” API security, you’re not alone. The confusion is baked into how these tools evolved and how they’re marketed today.
Both operate at Layer 7, the application layer, and both are usually deployed at the network’s edge. To make things trickier, cloud providers often bundle them together. In AWS, for instance, WAF rules can sit directly in front of an API Gateway. In Azure, the “Application Gateway” can run in WAF mode. It looks like a single control plane, so naturally, teams assume it’s a single tool doing both jobs.
But what’s really happened is an overlapping language, not a single function.
- Modern WAFs now inspect JSON payloads and API-specific parameters, stepping slightly into the API world.
- Gateways, on the other hand, have added basic threat filters – simple regex checks, bot mitigation, or anomaly detection – stepping slightly into the WAF world.
- Marketing teams from both sides have happily adopted the same buzzwords: “API protection”, “edge defense,” and “zero trust enforcement”.
The result? Two very different tools now sound eerily similar.
To add to the confusion, the industry now uses the term WAAP (Web Application and API Protection), which bundles WAF-like and Gateway-like features. But combining tools doesn’t automatically create visibility. More on this later.
The easiest way to separate WAFs and API Gateways is to remember the question each one asks:
- A WAF asks: “Is this request safe?” It’s looking for malicious payloads.
- An API Gateway asks: “Is this request allowed?” It’s enforcing access and policy.
Both questions matter, but they’re not interchangeable.
And here’s where the objectiv complexity begins.
Because APIs today aren’t static pages or simple calls. They’re living ecosystems, with chained requests, contextual tokens, and dynamic intent. In that world, safety and permission often blur.
That’s where the confusion deepens. The reality is, you don’t need two separate systems doing half the job. You need one that understands both the request and its intent. That’s what we built AppSentinels to be.
How the Divide Happened: A Short Evolution Story
To really understand why WAFs and API Gateways diverged, we need to rewind a little. The confusion wasn’t caused by bad design. It was born out of evolution.
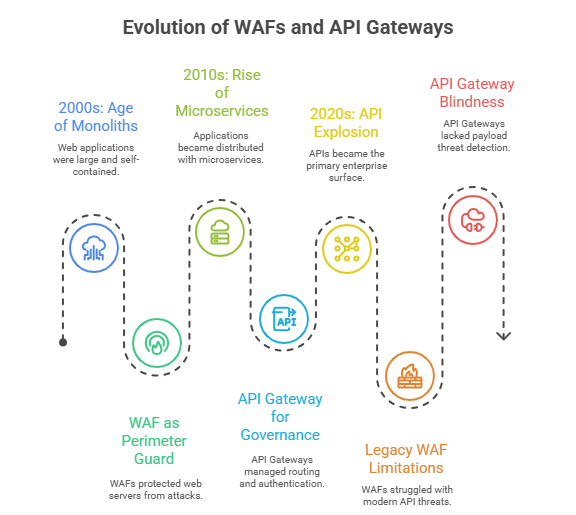
2000s: The Age of Monoliths
Web applications were large, self-contained, and lived inside data centers. Security meant protecting the perimeter.
The WAF was the perfect guard for that era: standing in front of web servers, inspecting traffic for SQL injections and cross-site scripting attacks. Everything passed through a single choke point.
2010s: The Rise of Microservices
Software stopped being monolithic. Applications became distributed – hundreds of microservices talking to each other over APIs.
Developers needed a way to manage routing, authentication, and version controlacrossn these moving parts. Enter the API Gateway.
It wasn’t built for security. It was built for governance and reliability, giving developers a single control plane for complex systems.
2020s: The API Explosion
Then APIs became the enterprise surface: connecting partners, mobile apps, and entire ecosystems.
But while APIs multiplied, legacy WAFs still operated on HTML and form data, noton JSON and GraphQL. They could block injection attempts, but couldn’t tell when a user misused valid credentials to exploit logic flaws.
API Gateways, meanwhile, managed access beautifully but stayed blind to payload threats.
Teams ended up running both, yet still missing attacks that lived between them.
“They began on opposite sides of the wall: one guarding monoliths, the other empowering microservices – until APIs erased the wall itself.”
When these two worlds collided, the very concept of an “edge” started to fade. Traffic no longer flows in a single direction or within a single fixed perimeter. APIs connect services across clouds, devices, and regions – and security can’t rely on static walls anymore.
Also read:
Cloud Implementation Patterns (AWS & Azure)
Let’s move from theory to reality. Here’s how WAF and API Gateway actually get deployed in the two most common cloud environments, and where the gaps show up in practice.
AWS Pattern: The Classic Chain
In most AWS deployments, the flow looks something like this:
AWS WAF → CloudFront → API Gateway → Lambda / backend services
Each piece serves a distinct purpose, but it’s easy to see where overlap and drift creep in.
- AWS WAF sits right at the edge, filtering Layer 7 payloads. It inspects requests for malicious signatures – SQL injections, XSS, known CVEs – and blocks what it knows to be dangerous.
- CloudFront, Amazon’s global CDN, then takes over, caching and distributing content closer to users. While primarily a performance tool, it can also pass along headers or metadata that influence downstream security rules.
- API Gateways handle routing, access control, and traffic shaping. It enforces rate limits, verifies API keys, manages stage variables, and integrates with identity providers for JWT or OAuth-based authentication.
- Finally, requests land at Lambda or an EC2 backend, where actual business logic executes.
The issue? Each layer is configured independently. WAF rules live in one console. Gateway policies in another. IAM configurations in a third. That’s where rule drift begins, when your traffic protection, routing logic, and identity enforcement slowly diverge over time.
It’s not that AWS lacks capability. It’s that without unified visibility, teams end up with parallel policies that don’t integrate.
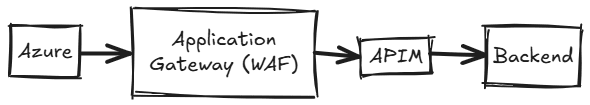
Azure Pattern: Integrated but Still Separate
Azure takes a slightly different approach, but the operational story is surprisingly similar.
- Azure WAF lives inside Application Gateway and is, tightly coupled with load balancing and traffic distribution. This simplifies deployment and gives admins fewer moving parts at the perimeter.
- Azure API Management (APIM), however, operates as a distinct service. It manages API lifecycle, versioning, developer portals, rate limiting, and analytics – but not deep security inspection.
- Many organizations chain Application Gateway (with WAF) → APIM → backend services.
On paper, this separation brings clarity. In practice, it still creates configuration gaps. Infrastructure-as-Code tools like Bicep or Terraform can define each layer neatly – WAF rules, API policies, routing paths – but runtime visibility remains fragmented.
Both clouds now push the “secure by design” narrative, embedding security controls across layers. Yet, security at runtime: understanding why an API behaved the way it did, not just what it did, is still missing.
Here’s what both patterns show: WAF + Gateway is no longer optionale. It’s the baseline for secure delivery. But without a single pane of runtime intelligence, the setup remains only half-aware of itself.
Where They Overlap. And Why That Matters
Here’s where things get tricky: WAFs and API Gateways don’t just coexist. They overlap.
Both operate at Layer 7. Both inspect HTTP traffic: headers, URLs, payloads, and tokens. Both generate logs. Both claim to “secure” your APIs.
So where’s the actual overlap?
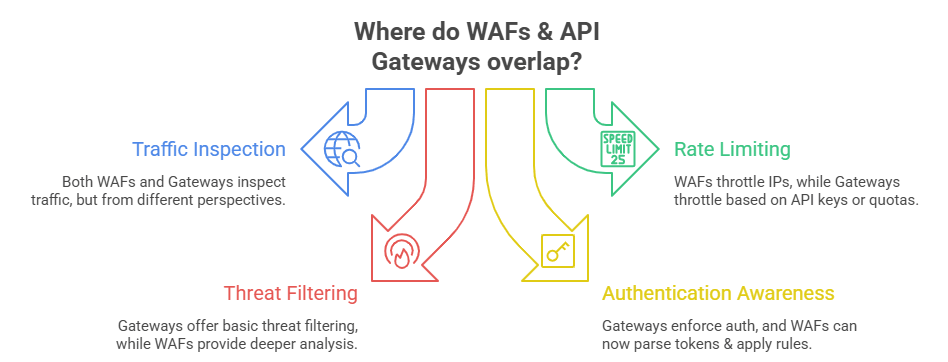
- Traffic inspection: Both see the exact requests flowing through, just from different angles.
- Rate limiting: WAFs can throttle suspiciothrottle suspicious IP addresses, base gateways, keys, or user quotas.
- Basic threat filtering: Modern Gateways now include simple regex checks or bot detection. WAFs have always done this, but deeper.
- Authentication awareness: Gateways enforce auth. WAFs can now parse tokens and apply rules based on claims.
On paper, this is defense in depth. In reality, it creates a dangerous illusion: each tool thinks the other is handling what it’s not.
The Real Problem
A WAF might flag a suspicious payload. A Gateway might verify it as properly authenticated. To each system, the request looks fine. But when you stitch them together? It’s a credential-stuffing attack in motion.
Think of two guards at a door:
- One checks for weapons (the WAF).
- The other checks the guest list (the Gateway).
Both do their jobs perfectly. Yet an insider still walks through.
That’s what happens when protection and permission are separated by design. Neither layer is wrong. Both are incomplete.
Common Blind Spots
- Token reuse across endpoints: A single valid API key is reused in ways it shouldn’t be, bypassing behavioral checks.
- Business-logic abuse: Transactions that look legitimate but exploit workflow weaknesses, like refund loops or permission escalations.
- Out-of-order API chaining: Attackers replay valid sequences in altered order to trigger unintended backend actions.
- Credential stuffing: Automated logins that appear “normal” because the structure and payloads are syntactically correct.
Each of these passes both guards, safe by content, allowed by policy, but malicious in pattern.
As APIs evolve into interconnected systems, mobile clients, partner integrations, and IoT devices, these overlaps become blind spots. Logs don’t correlate. Alerts don’t aggregate. And “defense in depth” quietly turns into “defense in disconnect”.
To truly understand why this keeps happening, we need to look beyond the edge: into how context-aware intelligence and runtime correlation close these gaps.
Modern Architectures: Why the Edge Isn’t the Edge Anymore
For years, security teams pictured the edge as a clear line. The front door of the network. Everything from outside gets inspected before entry. Simple.
That picture no longer fits.
In cloud-native architectures, there’s no single edge. Your APIs no longer serve external users. They connect microservices, mobile apps, partner systems, and internal tools. Each interaction is a potential exposure point.
Here’s the problem: most of your traffic never touches the edge.
Service-to-service calls, the kind that happen inside your cluster or between cloud regions, bypass your WAF and API Gateway entirely. These internal flows, often called east-west traffic, were never part of the original perimeter security model. Your edge tools were built to inspect north-south traffic, requests coming in from outside, not the mesh of internal API calls that power modern systems.
Add service meshes like Istio or Linkerd into the mix, and you’ve got invisible internal APIs handling discovery, routing, and load balancing, none of which your WAF or Gateway ever sees.
The result?
Your WAF and Gateway are guarding the front door. But most of your traffic is using the side entrance, the back hallway, and the fire escape.
Security tools that only watch the perimeter can’t protect what they can’t see. And in distributed architectures, the perimeter is everywhere and nowhere at once.
“In a mesh of APIs, the edge isn’t a line. It’s a moving field where data and behavior constantly trade places.”
The edge hasn’t disappeared. It’s dissolved into the application itself. And that changes everything about how you secure it.
Where the Cracks Show
Deploying both a WAF and an API Gateway doesn’t guarantee security. In fact, it often creates a false sense of coverage, where each tool assumes the other is handling what it’s not.
Here’s where that illusion breaks in practice.
Scenario 1: The Token That Looks Fine
A user authenticates successfully. The API Gateway verifies the JWT token, checks the signature, and confirms the user has access. Request approved.
Meanwhile, the WAF inspects the payload. Clean JSON. No SQL injection. No XSS. No known attack patterns. Request passes.
But neither tool notices that the same token is being reused across points in 90 seconds, scraping data it technically has access to, and it technically wouldn’t be pulling in bulk.
The Gateway saw valid auth. The WAF saw clean syntax. The attack succeeded.
Scenario 2: The Mutation That Slipped Through
Your WAF is tuned for REST APIs. It knows how to parse query strings, form data, and simple JSON bodies. It’s good at spotting DROP TABLE or <script> tags.
Then a GraphQL mutation comes through. Nested, layered, with variables injected three levels deep. The WAF sees JSON. It doesn’t understand the query structure. It passes.
The Gateway routes it correctly, no problem there. But it doesn’t inspect payloads, that’s not its job.
The mutation modifies user permissions. No signature matched. No policy blocked it.
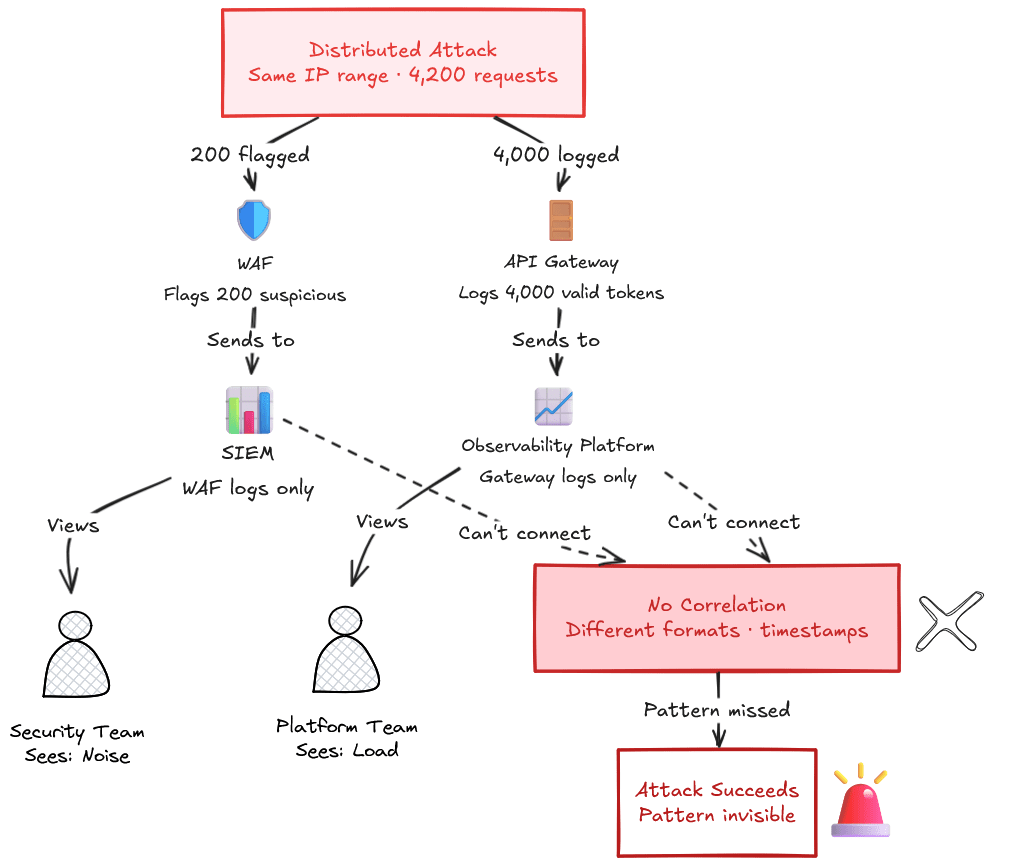
Scenario 3: The Logs That Don’t Talk
Your WAF flags 200 suspicious requests in an hour. Your Gateway logs show 4,000 requests from the same IP range during that same window, all with valid tokens.
But the WAF logs live in your SIEM. The Gateway logs live in your observability platform. Different formats. Different timestamps. No correlation.
Your security team sees noise. Your platform team sees load. Nobody considers the distributed attack playing out across both layers.
Also check out:
The Pattern Repeats:
Each tool does its job. Each tool sees part of the picture. But the space between them, where intent hides, and behavior reveals itself, stays invisible.
That’s not a configuration problem. It’s an architecture problem. And it’s precisely where attackers have learned to live.
Case Study: When Both Guards Miss the Intruder
Let’s turn theory into reality.
In 2021, Experian, one of the largest credit bureaus in the U.S., exposed the credit scores and risk profiles of millions of Americans. Not through a hack. Not through a breach of their core systems. But through an API that was working exactly as designed.
The Setup
Experian provided credit-scoring APIs to credit scorers, lenders, insurers, and other businesses that needed to assess creditworthiness.Assesse APIs were meant to be secured by intendedartners integrating them.
Exper who managed the structure included standard protections: firewalls, access controls, and authentication layers. On paper, the setup looked solid.
The Exploit
Security researcher Bill Demirkapi discovered that one of these partner sites had integrated Experian’s API without proper authentication. The API returned sensitive data, including credit scores, risk factors, credit indicators, and name and address.
Some checks, like birthdate validation, were either weak or bypassable entirely. That meant anyone with basic information could query the system and pull credit data for virtually any American.
The API itself wasn’t compromised. The payloads were clean. The requests were structured correctly. Everything looked legitimate.
But the authentication layer, the part that should’ve verified who was asking and why, was either missing or so weak it didn’t matter.
What the Tools Saw
If a WAF were inspecting those requests, it would’ve adequately seen formatted API calls. No SQL injection. No XSS. No malicious payloads. Cleared.
If an API Gateway were managing access, it would’ve verified that requests were coming from a recognized partner endpoint. Valid route. Allowed traffic. Approved.
Both layers did their jobs. Yet anyone could enumerate credit scores at scale.
What Went Wrong
Security didn’t fail because Experian’s infrastructure was weak. It failed because the system relied on partner-level controls that were never validated or monitored at runtime.
The API worked as designed. The Gateway routed correctly. The WAF found no threats. But nobody was watching how the API was being used, whether access patterns made sense, or if the same inputs were being queried repeatedly from suspicious sources.
By the time the vulnerability was discovered and the endpoint shut down, the exposure had already happened. And concerns remained: how many other partner integrations had the same gaps?
Then there was, of course, the infamous Optus breach. We covered it in detail here.
The Lesson
Security broke not because a tool failed. It broke because the tools never talked to each other. The WAF saw clean payloads. The Gateway saw valid routes. Neither noticed the behavior. And that’s where millions of records walked out in plain sight.
The Real Problem: Asking the Wrong Question
This is where most teams lose the plot.
After every breach, someone inevitably asks: “So do we need a stronger WAF or a smarter API Gateway?”
That’s the wrong question.
Because no matter how sharp your rules are, or how tightly your API Gateway enforces tokens, attackers are no longer token validation walls. They’re slipping through the spaces between them.
In today’s API-first world, the question isn’t “Which is better?”
It’s “How much context do you see between them?”
Why Better Tools Aren’t Enough
Most teams spend months optimizing configurations: tuning WAF rulesets, setting gateway quotas, tightening authentication.
Some vendors have tried to simplify this with WAAP (Web Application and API Protection), platforms that bundle WAF and a way-like features into one offering. On paper, it sounda singleike the answer: one tool, one console, unified controls.
But bundling features doesn’t automatically create visibility.
A WAAP might inspect payloads and enforce rate limits in the same platform. But it still sees traffic request by request, with no memory of what happened five minutes ago or across different endpoints. It doesn’t see behavioral relationships across calls: who’s using what token, how frequently, fromwhichre, or with oftenrn.
And that’s exiny what attackers exploit. They chain valid calls, replay tokens, and stretch business logic until it breaks.
The Real Shift
Even the most sophisticated tools can fail when they don’t communicate because security isn’t about rules. It’s about relationships. It’s not about building higher walls. It’s about building awareness between them.
The moment you start correlating intent, traffic patterns, and identity context across those walls, you stop chasing isolated alerts and start understanding the full attack story.
And that’s where the next evolution of security begins: a new layer of intelligence that doesn’t just watch for bad packets, but understands behavior across both guards.
That’s not a WAF problem,r a Gateway problemym or even a WAP problem. It’s a isibility problem.
And that’s exactly what AppSentinels was built to solve.
The AppSentinels View: Unified Context Security
If a WAF filters what’s dangerous and an API Gatewout ay manages what’s allowed, AppSentinels exists to understand why something happeto, and whether it makes bushappensense.
Most tools see half the picture. WAFs watch payloads. Gateways watch paths. Neither understands business logic: the workflows, user journeys, API sequences, and object relationships that define legitimate behavior.
That’s where attacks hide, not in malicious payloads or missing tokens, but in valid requests doing invalid things.
How It Works
AppSentinels builds a deep understanding of your application’s business logic by:
- Discovering every API, including shadow, orphan, zombie, and LLM APIs
- Tracking complete user sessions and lifecycles
- Learning context and intent, why an API is called, not just what it does
- Mapping API sequences and detecting out-of-order calls
- Understanding roles, behaviors, and authorization boundaries
- Distinguishing legitimate edge cases from malicious abuse
It continuously learns behavioral baselines with real-time risk scoring. When behavior deviates, token reuse, out-of-sequence calls, unauthorized AI agent actions, the system detects it immediately through AI-driven analytics. No signatures. No predefined rules.
AppSentinels transforms fragmented insights into a living security model that adapts with every request, protects against AI-era threats, and scales to 100B+ API calls monthly without performance impact.
“Security used to stop at the edge. With AppSentinels, it starts at understanding, and protects the business logic layer where modern attacks actually happen.”
Frequently Asked Questions (FAQs) on WAFs & API Gateways
1. Can a WAF protect GraphQL APIs effectively?
Traditional WAFs struggle with GraphQL because they’re built to inspect REST patterns. GraphQL queries can be deeply nested with variables injected multiple layers down, making it hard for signature-based detection to parse malicious intent. You need tools that understand GraphQL schema, query depth, and resolveschemaserns, not just HTTP payload structure.
2. Do I need both a WstructuresI Gateway for internal APIs?
It depends on your architecture. Internal APIs between microservices (east-west traffic) often bypass traditional edge tools entirely. If your services communicate within a mesh or private network, you need runtime API security that monitors behavior and business logic at the service layer, not just perimeter-based filtering.
3. How does API security differ from web application security?
Web application security focuses on protecting user-facing interfaces from attacks like XSS and CSRF. API security deals with machine-to-machine communication, token lifecycles, rate limiting, data exposure through endpoints, and business logic abuse. APIs expose more granular data access and lack the visual context that makes web attacks easier to spot.
4. What’s the difference between API Gateway and API Management?
An API Gateway handles runtime traffic, including: routing, authentication, and rate limiting. API Management is broader; it consists of the entire API lifecycle, such as design, documentation, developer portals, versioning, analytics, and monetization. Gateway is the execution layer,and Management is the governance layer.
5. Are serverless APIs harder to secure than traditional APIs?
Yes and no. Serverless functions scale automatically and reduce infrastructure overhead, but they create ephemeral, distributed endpoints that traditional security tools can’t easily monitor. You lose visibility into function-to-function calls, IAM misconfigurations become more common, and cold start behaviors can bypass rate limits. You need security that understands serverless event patterns and function invocation chains.
6. How do you secure APIs exposed to AI agents and LLMs?
AI agents operate differently from human users. They can call APIs in rapid, unpredictable sequences, attempt to use workflow shortcuts, or generate invalid requests. Securing them requires behavioral monitoring that understands agent intent, validates tool use permissions, and detects when agents deviate from expected interaction patterns. Traditional auth and rate limiting aren’t enough.
7. What is BOLA/IDOR, and why do WAFs miss it?
BOLA (Broken Object Level Authorization), also called IDOR (Insecure Direct Object Reference), occurs when an API allows users to access objects they shouldn’t, such as viewing another user’s order by changing an ID in the URL. WAFs miss this because the request structure is valid and authenticated. The vulnerability is in business logic and object ownership, not in the payload syntax.
Conclusion: From Layers to Intelligence
The debate was never really WAF vs API Gateway. They were never meant to compete, only to complement. One guards the syntax of the request, the other governs its journey. But real security in 2026 depends on what happens between them.
That’s where visibility defines resilience. When each layer operates in isolation, attackers exploit the blind spots between the walls. When context unites them, security shifts from reaction to anticipation.
Because the modern perimeter isn’t hardware or software anymor,pt’ss understanding. It’s how intellanymorey it’ssystems can read intent, correlate behavior, and adapt in real time.
The teams that win aren’t the ones with the most tools. They’re the ones who connect what their tools already see.
Security maturity in 2026 isn’t about stacking more walls. It’s about linking what your walls already see, and building the intelligence layer that turns fragmented signals into unified awareness.
That’s not just better security. That’s the only security that scales with modern APIs.